Embedded wallets — What are they and how Apillon redefines the concept

Embedded wallets, embedded accounts, wallet as a service, e-mail wallets, smart wallets, in-app wallets, social wallet, Web3 wallet, account abstraction. All these terms can, in most cases, be used interchangeably to describe more or less the same thing.
But what is it they are describing? To explain that, we need to understand wallets in general.
First things first — What is a wallet?
A wallet is simply a user interface that allows you to easily generate and sign transactions using your private key. As such, a wallet also takes care of storing your private key.
Private key storage and management are extremely important. Your private key is the only way you can access your crypto. If you lose your private key or it gets stolen, your assets will also be lost/stolen.
Since the private key is the wallet's main element, different types of wallets are named by how they handle the key.
- Hot wallets are very convenient and are used frequently. However, due to their direct connectivity to the Internet, they can be accessed and managed by hackers. MetaMask is an example of a hot wallet. It’s an internet browser extension used on a computer with internet access. If a hacker gets access to your computer, they can steal your private key and all your crypto.
- Cold wallets, on the other hand, offer a high level of security since they don’t provide access to the Internet. However, they are also less convenient than hot wallets. To initiate a transaction, you need to sign the transaction parameters with your private key. For example, you can have a phone or computer that never connects to the Internet and still securely sign the transaction, move the signed transaction to a device with access to the Internet, and send it to a blockchain node.
- Hardware wallets deliver both convenience and higher security compared to cold wallets. These specifically designed physical devices contain secure chips that store private keys, and even if someone physically steals the device, they cannot access the private key. Hardware wallets can be connected to a hot wallet like MetaMask, providing a relatively good user experience while eliminating the risk of a private key being stolen or compromised.
These types of wallets are most commonly used for managing crypto. However, their main problem is the clumsy user experience of setting up a wallet and protecting the private key.
Regardless of the type, a user first needs to download and install a wallet, then create a backup of the private key in mnemonic form, either written on paper or digitally (and less secure) in a password vault. This alone creates two barriers to entry before the user even gets to acquire crypto assets.
But there is a way out.
Embedded wallets
Embedded wallets or account abstraction wallets tackle the inelegant onboarding process by eliminating the clumsiest parts: wallet download and installation.
How they do that is the interesting bit.
They come with an integration SDK that allows developers to directly embed them (hence the name) into an app or website they’re building.
Also, they abstract away (hence the other name) private key management by adding authentication methods and private key splitting. This way, developers can improve the app onboarding experience by allowing users to log in and access the embedded wallet by simply using their email and a code sent via email. No need to download anything or save any kind of mnemonic phrase.
What about drawbacks?
Depending on the provider, embedded wallets might come with certain drawbacks.
First, embedded wallets are only available on sites or apps where developers have already integrated them.
Second, embedded wallets are app/site-scoped, not globally scoped, like hot wallets. So if two dapps or sites have integrated the same wallet provider, users can log in with the same email but can only access site-based assets. Similarly, they cannot use the funds from one site on a different site without first transferring them.
Third, in embedded wallets, security could get compromised to some extent. The private key in embedded wallets is, indeed, safely sharded, encrypted, and stored when not used. However, once a user signs into a site or a dapp, the private key could get exposed in the Internet browser, much like in a hot wallet, and potentially hacked.
Choose wisely
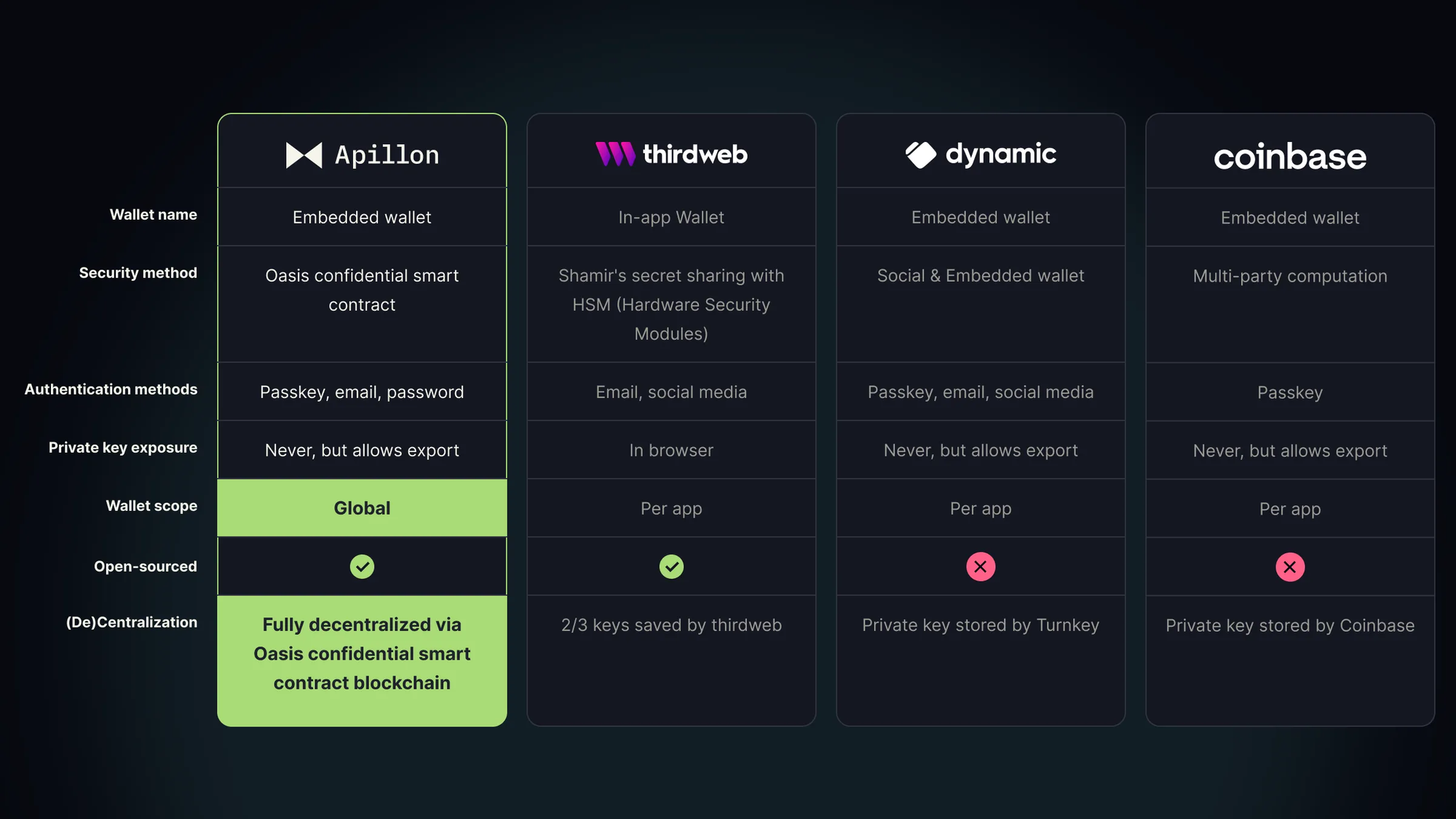
To illustrate the differences between embedded wallets, let’s look at a few wallet providers, their security models and how they operate.
Apillon’s embedded wallet
Compared to the providers listed above, Apillon’s embedded wallet powered by Oasis resolves the drawbacks of other embedded wallets.
How so?
First, the (de)centralization part. Aligned with Web3 principles, it was important for us to move private key management from central setups and, instead, leverage a decentralized network, such as Oasis, and its smart contract privacy.
Oasis delivers confidential smart contracts with end-to-end encryption. Through Oasis, we have created smart contracts that generate and store private keys that are fully encrypted, never exposed, non-custodial, and completely decentralized. This means that end users need not rely on any third-party service to store their private keys. Users can control their own authentication methods by adding various passkeys, password (though not recommended), email login, etc., to access their wallet.
Second, the transactional security part. When a user initiates a transaction, its parameters are sent directly to the smart contract along with the authentication challenge that authorizes the user. The transaction gets signed directly in the smart contract and sent to a blockchain node. This way, the private key is never exposed — much like by using a hardware wallet.
Convenience meets security
In a nutshell, the UX benefits of Apillon’s embedded wallets are paired with the decentralization and security of hardware wallets. Besides, users don’t need to rely on any third-party provider like Coinbase or Turnkey to securely store and back up their keys.
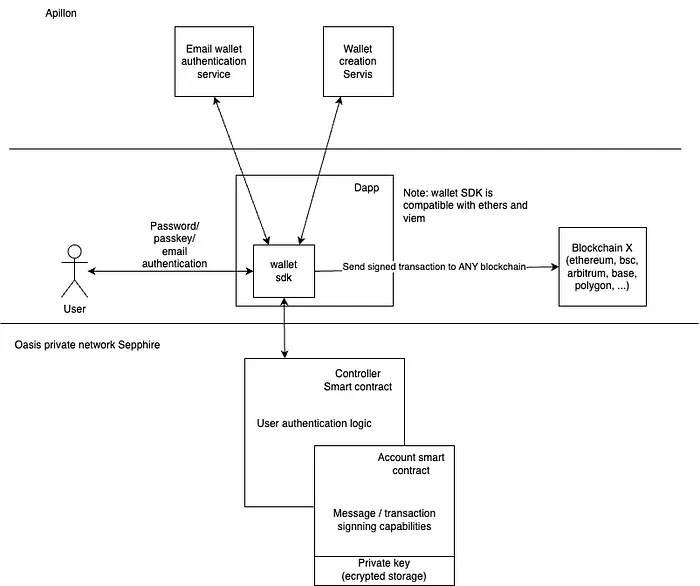
With this embedded wallet design, Apillon delivers UX convenience to the Oasis network, allows gasless wallet creation through smart contract deployment, and runs the email authentication service.
The underlying wallet and authentication methods, like passkey, are fully decentralized and not dependent on any external system.
Stay tuned for Apillon’s embedded wallet release in a couple of weeks.
⧓ About Apillon
The Apillon platform serves as a unified gateway to the Web3 services provided by linked Polkadot parachains. Following the multi-chain vision, Apillon powers the transition of developers to Web3, simplifying its adoption in the real economy, and expanding its versatility as the ecosystem grows. With Apillon, Web3 services are within reach for every developer, regardless of their background and experience with blockchain technology.
Website | Wiki | GitHub | X | Discord | LinkedIn | Reddit | Telegram

